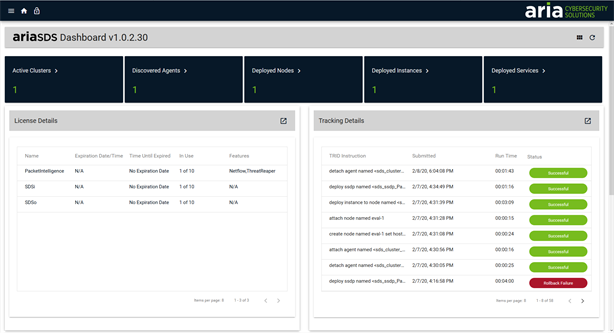
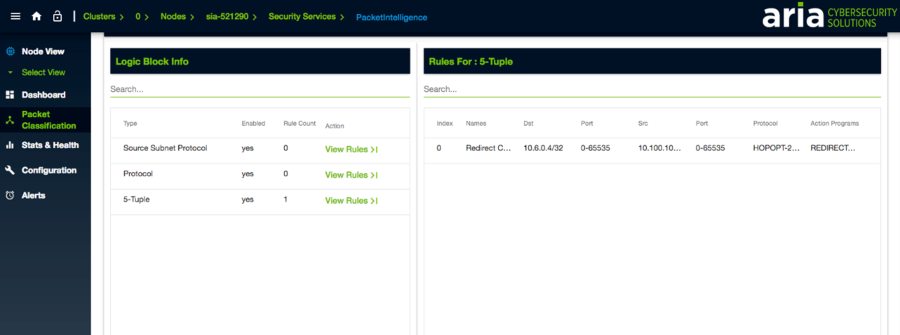
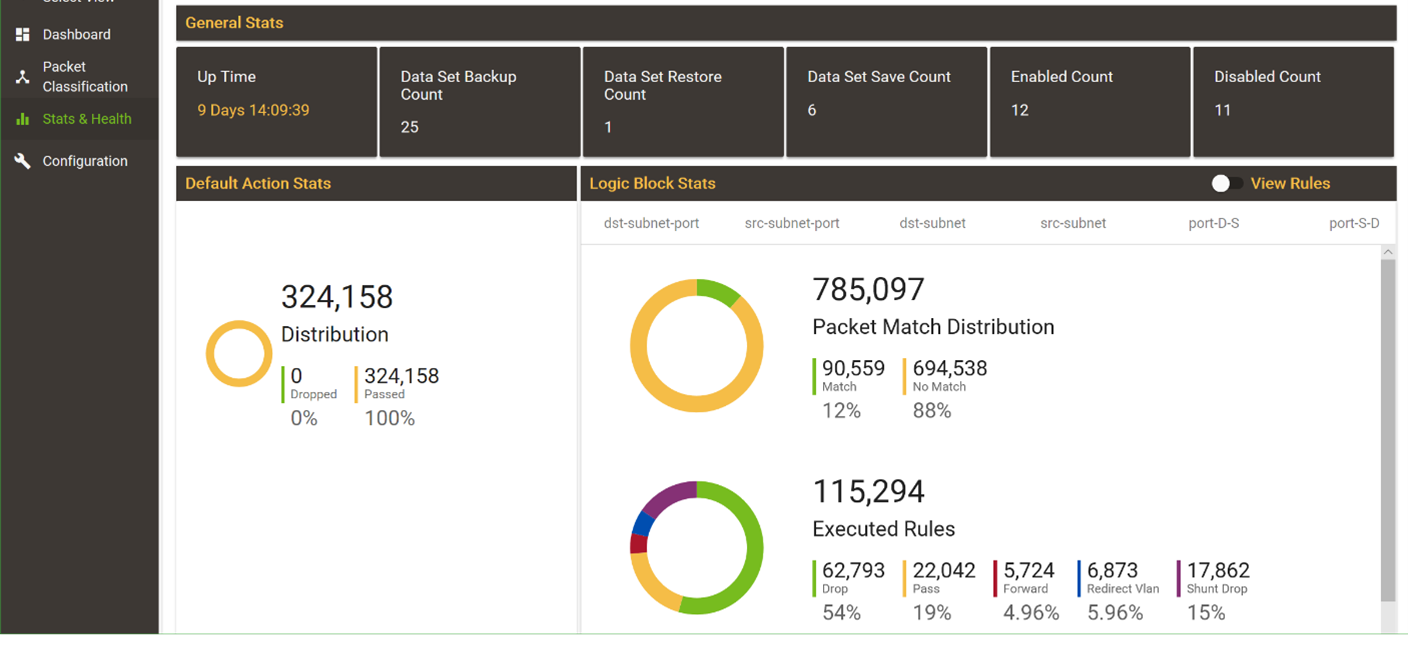
ARIA SDS Packet Intelligence
Network Analytics and Cybersecurity Control—in One Powerful Application
Wire-Rate Packet Operations for Advanced Network Analytics and Improved Security Controls
The ARIA Packet Intelligence (PI) application gives OEMs, service providers, and security professionals a better way to use SmartNIC technology to support two important use cases: advanced packet-level network analytics and cyber-threat detection, response, and containment.
Network analytics: ARIA PI provides complete visibility into all network traffic and feeds valuable analytics data to packet delivery accounting tools, quality of service systems, and SLA monitoring applications. All of this helps companies provide better service and maximize revenues tied to usage-based billing.
Cyber-threat detection, response, and containment: ARIA PI also feeds metadata to threat detection tools for complete visibility into all network traffic, including east-west data flows. This improves the effectiveness of existing security solutions, such as SIEMs and IDS/IPS tools, and gives security teams a better way to detect, respond, contain, and remediate even the most advanced cyber threats.
ARIA Packet Intelligence Benefits

Improve Network Analytics
Feed analytics data to packet delivery tools, SLA applications, and more.
Complete Network Visibility
Perform full network monitoring of all assets and application data.

Automate Response
Improve investigation effectiveness and threat containment.

Improve Security Posture
Enhance security operations with accurate and timely threat detection, investigative response, remediation and build high-speed firewalls.

Reduce Costs
Quick, simple deployment that is cost-effective to operate.

Detect More Cyber Threats, Faster
Enhance existing security tools to expose and identify typically missed threats for faster incident detection and response and fewer false positives.
Packet Intelligence Offerings
-
Accounting and Network Enforcement

-
Threat Detection & Investigative Response

-
Network-Based Threat Remediation

-
High-Speed Firewall

The ARIA PI application offloads packet counting and classification capabilities onto the Myricom SIA SmartNICs and can easily enforce policies such as rate limiting. In addition, ARIA PI can perform critical operations such as packet marking or tagging for packet accounting and SLA enforcement, while maintaining wire rates of up to 100Gbps.
Threat Detection
Deployed through either a network tap or span switch, or in-band, the Triage configuration can direct traffic streams to applications for counting packets, monitoring QoS SLAs, as well as threat detection toolsets, which allows for faster IR with more complete identification and verification of threats. It offers intelligent filtering capabilities to direct only the appropriate classified traffic streams to security toolsets. Such adaptive filtering allows detection tools to operate more effectively by only analyzing the most relevant threat conversation traffic.
Threat Investigative Response
The ARIA PI application classifies every packet traversing the network, allowing security teams to redirect specific traffic conversations for further analysis. They can direct copies into an IDS, or conversely, redirect the original packet stream to an IPS for a closer look before sending to their destination. In parallel, any suspicious streams can be copied and directed to packet recorders for even further analysis or recording for later forensic inspection.
ARIA PI enables the real-time, automatic execution of remediative actions on specified traffic flows including:
- The creation, application, and enforcement of microsegmentation policies.
- The identification and containment of threat traffic by redirection to security tools as specified by policies.
- Leverage automated workflows automation, in tools such as SOARs, for additional investigation by redirecting threat traffic.
The ARIA PI application can assist OEM organizations in the construction of cost-effective, high-speed firewalls. When deployed on the Myricom SIA PCIe SmartNIC, the application avoids the need for upgrade or “rip and replace, as it can be easily deployed in commercial servers or OEM appliances.
- Runs at full 10G, 25G, or up to 100Gbps wire rate without impacting network or application performance
- Offloads packet handling to scale OEM and service provider applications
- Deploys easily with simple API connectors to OEM and service provider applications
- Meets a wide variety of wire-rate network service monitoring and control functions, as well as cybersecurity requirements
- Provides visibility into all network traffic for full network monitoring of all critical assets and application data, including lateral traffic flow
- Allows for the setting and enforcement of network policies
- Improves the threat detection and containment effectiveness of security tools, including SIEMs, IDS/IPS, and forensic packet recorders
- Stops network-borne threats by isolating infected devices or dropping harmful traffic
OEM Order Details
Please see below:
| Model Number | Product Description |
|---|---|
| 25G-PCIE3-8C-PACKAN | Myricom SIA Express – Dual 10/25G low-profile, (HHHL). Includes 16 GB of DDR4 memory. Perpetual license, ARIA Packet Intelligence, Accounting and Network Enforcement |
| 100G-PCIE4-8D-PACKAN | SIA – Dual 25/50G Security Intelligent Adapter (low profile). Includes 16 GB of DDR4 memory. Perpetual license, ARIA Packet Intelligence, Accounting and Network Enforcement |
| SPT-PACKAN-LIC | Annual support for ARIA Packet Intelligence, Accounting and Network Enforcement – software updates and email support. |
| 25-PCIE3-8C-PI | Myricom SIA Express – Dual 10/25G low-profile, (HHHL). Includes 16 GB of DDR4 memory. Perpetual license for ARIA Packet Intelligence Software. Complete Packet Intelligence Suite. This bundle combines all of the features provided by Threat Analytics, Threat Investigation and Threat Remediation. |
| SPT-PI-PRO | PI-Pro – Annual Support – software updates and email support. |
| Contact Factory | Annual license, ARIA Packet Intelligence, Stateless Firewall Offload |
| SDS-SDSo-LIC-Perpetual | SDSo Perpetual license for SDS Orchestrator Software. Manages an unlimited number of deployed instances. Required for HA configuration. |
| SPT-SDSo | Annual support for SDSo SDS Orchestrator Software. Manages an unlimited number of deployed instances. Required for HA configuration. – software updates and email support. |
| SDS-SDSo-L-LIC-Perpetual | SDSo Light Perpetual license for SDS Orchestrator Software. Manages up to 10 deployed instances. |
| SPT-SDSo-L | Annual support for SDSo LightSDS Orchestrator Software. Manages up to 10 deployed instances. – software updates and email support. |
| OEM Datasheet | See OEM product datasheet. |
Direct Sales Order Details
| Model Number | Product Description |
|---|---|
| 25G-PCIE3-8C-PACKAN | Myricom SIA Express – Dual 10/25G low-profile, (HHHL). Includes 16 GB of DDR4 memory. Perpetual license, ARIA Packet Intelligence, Accounting and Network Enforcement. |
| 100G-PCIE4-8D-PACKAN | SIA – Dual 25/50G Security Intelligent Adapter (low profile). Includes 16 GB of DDR4 memory. Perpetual license, ARIA Packet Intelligence, Accounting and Network Enforcement. |
| 25G-PCIE3-8C-PI | Myricom SIA Express – Dual 10/25G low-profile, (HHHL). Includes 16 GB of DDR4 memory. Perpetual license for ARIA Packet Intelligence Software. Complete Packet Intelligence Suite. This bundle combines all of the features provided by Threat Analytics, Threat Investigation and Threat Remediation. |
| SDS-SDSo-LIC-Perpetual | SDSo Perpetual license for SDS Orchestrator Software. Manages an unlimited number of deployed instances. Required for HA configuration. |
| SDS-SDSo-L-LIC-Perpetual | SDSo Light Perpetual license for SDS Orchestrator Software. Manages up to 10 deployed instances. |
Featured Resources

Flow-level security analytics for tools like SIEMs or the ARIA ADR application.
Contact Us to Speak to a Cybersecurity Expert!
Resources and Related Content
Resources
Blog
News
ARIA Cybersecurity Solutions, a leading provider of cybersecurity solutions, recognizes Information Systems for Trading (IST) as a premier reseller in the Jordan and Iraqi…
ARIA Cybersecurity Solutions has joined Rockwell Automation’s PartnerNetwork™ as a Technology Partner. Through PartnerNetworkTM, customers can quickly locate complementary products that best solve application…
ARIA Cybersecurity Solutions, a CSPi business (NASDAQ: CSPi), has announced that its breakthrough solution for protecting Operational Technology (OT) environments, AZT PROTECT™, has won…
Events