Myricom SmartNICs
Purpose Built for Optimal Performance
Accelerate Application Performance, Offload Cybersecurity Features, and Improve Network Analytics
The Myricom line of SmartNICs improves server and application performance by offloading a variety of server-intensive functions, such as cybersecurity functions like encryption and micro-segmentation. This is in addition to our track record of providing industry-leading timestamping at line rate and with zero-loss packet capture.

Myricom Network Adapters capabilities and benefits:
Increase server and application performance by offloading a variety of core-intensive functions, including cybersecurity features
Run native applications, third-party applications, and ARIA SDS applications for enhanced network security.
Improve network monitoring and analytics with less effort and more accuracy, using precise hardware timestamps on both ingress and egress packets.
Myricom solutions are ISO 9001 Certified
Members of the Myricom Series
-
ARC C-Class and D-Class
 Low profile PCIe, ASIC or FPGA
Low profile PCIe, ASIC or FPGA
-
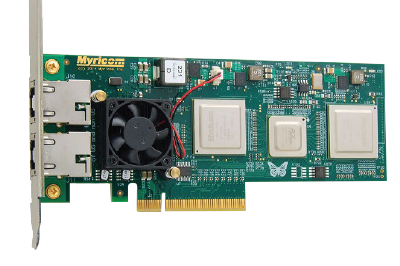
ARC-E Class
 Low-profile PCIe – Xilinx FPGA
Low-profile PCIe – Xilinx FPGA
-
Myricom SIA
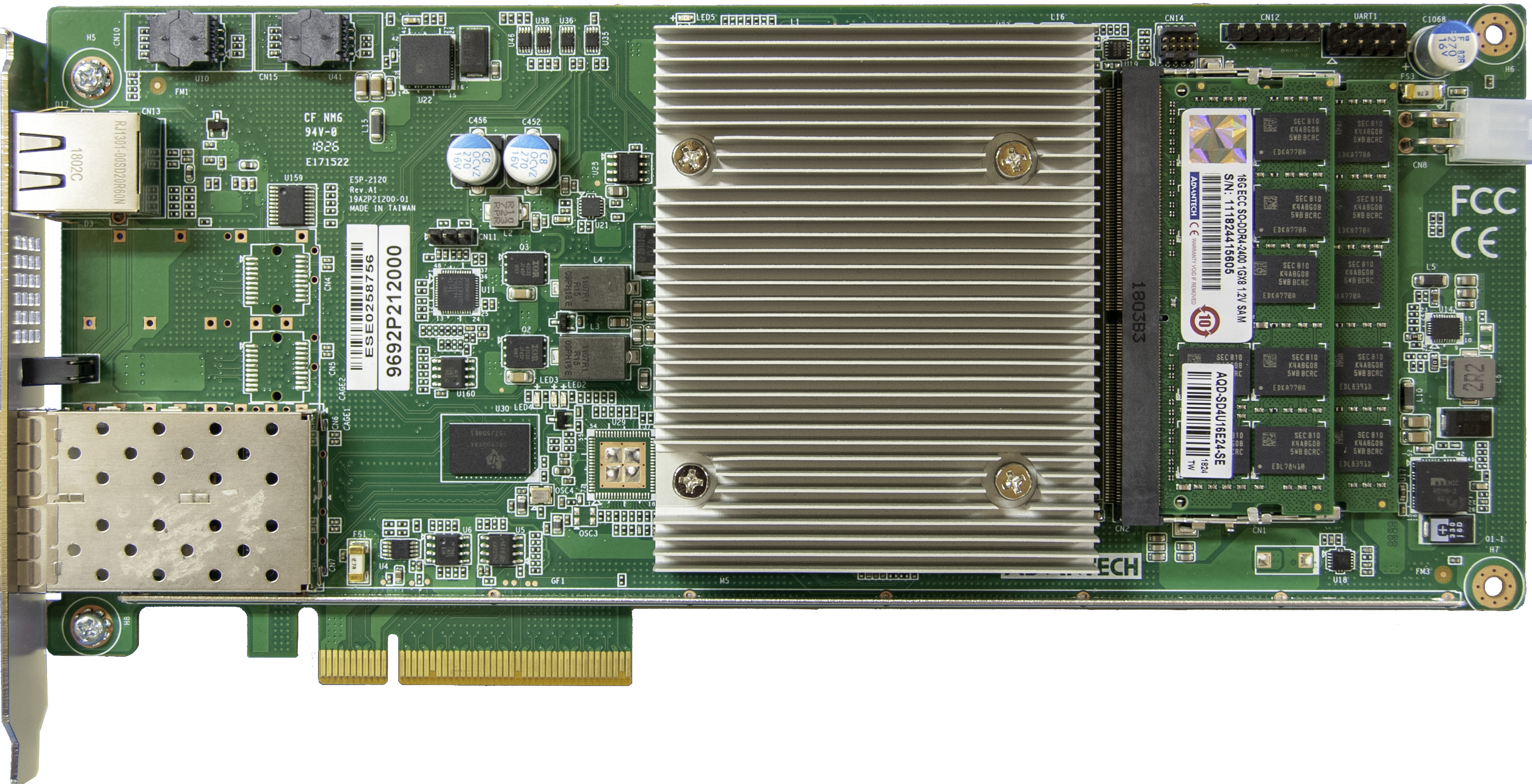
Full-height PCIe – ARM Core
-
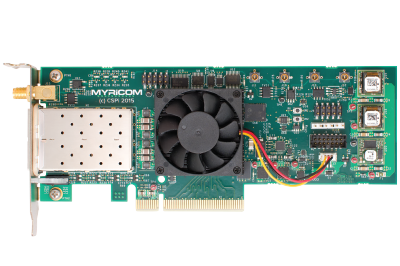
Myricom SIA Express
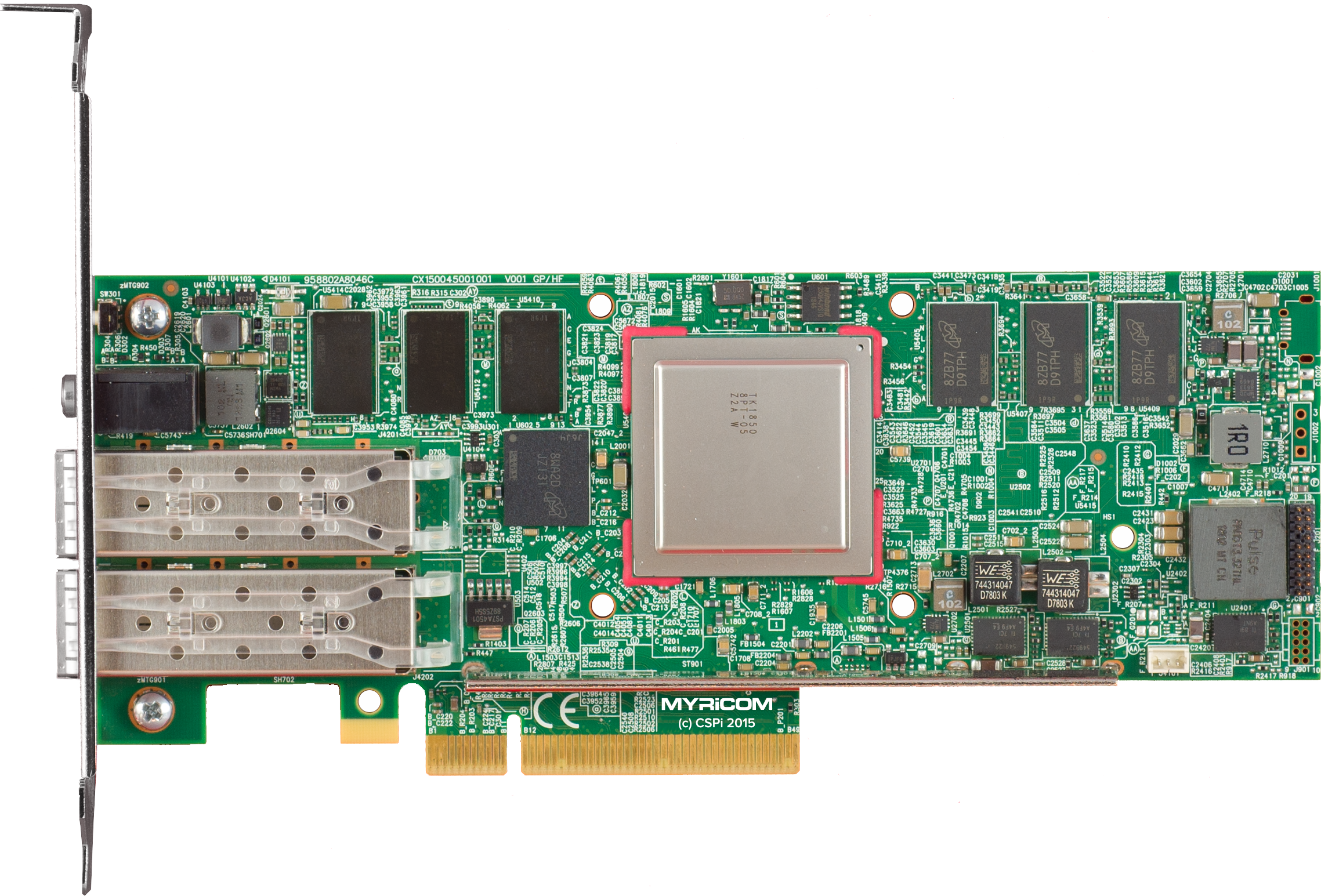 Full-height PCIe – ARM Core
Full-height PCIe – ARM Core
ARC C-Class
A powerful, low-cost option for dropless packet capture, at 10GB line-rate, and low-latency transfer. Appropriate for a number of industries where network monitoring or transactions are critical, including automated financial trading, content creation, and network intelligence. The C-Class is popular in open-source communities with multiple plug-ins. It also works as a standard NIC for non-capture applications.
ARC D-Class
For financial firms demanding high performance and reliability, the D-Class is a low-cost, fully functioning 10 GbE network adapter. With DBL, a tightly integrated combination of FPGA firmware and software, the D-Class drives down system-level tick-to-trade latency and enables advanced financial trading capabilities. Unique application-enhancing features include extremely accurate timestamping on both “receive” and “send” network packets.
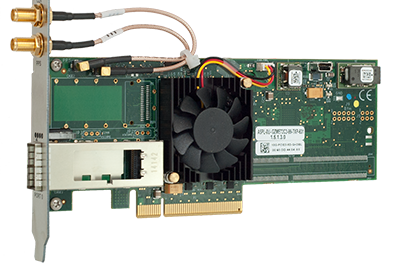
For financial firms demanding high performance and reliability, the D-Class is a low-cost, fully functioning 10 GbE network adapter. With DBL, a tightly integrated combination of FPGA firmware and software, the D-Class drives down system-level tick-to-trade latency and enables advanced financial trading capabilities. Unique application-enhancing features include extremely accurate timestamping on both “receive” and “send” network packets.

The E-Class uses an optimized combination of hardware, FPGA firmware, and software libraries to deliver application-specific functionality in a cost-effective package. With the E-Class, you get all the functionality of the C-Class with additional hardware offloading functionality for scaling, including parsing capabilities for tunneling protocols like GTP/GRE.

The Myricom Secure Intelligent Adapter (SIA) combines the functionality found in a next-generation high-speed network adapter with the programmability of a multi-core ARM processor to provide flexible application-specific feature support. The capabilities of this 10GB or 25GB dual-port adapter card opens new possibilities for accurate threat detection and disruption, without impacting network performance.

The Myricom Secure Intelligent Adapter (SIA) Express dual-port 25G integrates powerful networking and processing subsystems for the offloading of CPU-intensive applications such as the encryption and decryption of DNS over HTTPs or TLS. This industry-standard half-height and half-length (HHHL) form factor is convenient for integration with data center servers. It also features a high-performance data center system on chip (SoC).

Use Cases

Data Protection and Network Visibility
Our Myricom adapters play a critical role in network visibility, which is critical to achieve enterprise-wide network security and data protection. It is now easier for security professionals to monitor network traffic, including east-west, to detect all network-borne threats, which are normally missed. The Myricom SIAs can easily handle the deployment of the ARIA security applications for enhanced network security, key management, packet capture and classification, as well as the offload of encryption functions.

Cybersecurity
Our Myricom SIAs are designed to solve today’s data center and cybersecurity challenges related to power consumption, scalability performance, and security. When running the ARIA™ SDS Packet Intelligence application on the Myricom SIA, you receive faster and more accurate network analytics that can be used for network monitoring, SLA enforcement, packet accounting, and threat detection and response. The Myricom SIA also provides a local secure zone of trust to store and run the encryption keys, which prevents the exposure of encryption keys in the event that the host server is breached.

Zero-Loss Packet Capture
Our Myricom SmartNICs, with Sniffer10G, are optimized for line-rate zero-loss packet capture, timestamping, and classification of all network traffic. All of this provides a key piece of the data protection and network visibility puzzle.
Resources and Related Content
Resources
Blog
News
ARIA Cybersecurity, a CSPi business (NASDAQ: CSPi) announced its first deployment within a major US Oil refiner’s critical OT infrastructure.
ARIA and Acronis host live event to demonstrate how AZT PROTECT™ can be used to extend the life of Windows 10 OT systems –…
ARIA Cybersecurity, a CSPi business (NASDAQ: CSPi) today announced a new feature set that allows OEMs to integrate patented AZT PROTECT™ into their products…
Events