Automated Breach Response
Complete breach investigation in hours and easily meet data privacy regulations
nVoy Series dramatically reduces time and effort of your breach response involving your critical assets
Automate breach verification and notification for critical assets.
Generate forensic evidence of the exact records breached, including if they were properly encrypted to avoid breach related costs.
Meet regulatory compliance requirements, such as HIPAA, 23 NYCRR 500 and GDPR’s 72-hour breach notification.
Automated Breach Response Products and Solutions
The Challenge
Why is Breach Response and Meeting Regulatory Compliance So Challenging?
Standard tools and best practice approaches – most notably threat hunting and breach prevention – are not effective in helping the organization achieve compliance. They fall short for a number of reasons:

Too Much Noise
InfoSec professionals receive over 5,000 intrusion alerts per day from their installed security tools.

Patching Can’t Keep Up
Patch efforts can take months, even even years between discovery and fix – and still lead to vulnerabilities.

Cost and Complexity
Today’s organizations have IT infrastructures that are highly complex, dynamic, and scalable.
The Solution
Automated Breach Response and Full Compliance Assurance
With nVoy Series, verified breach detection and notification is automatic.
It not only tells you of successful attacks on your critical applications, it tells you the exact data records exposed.
100% data recording and breach-triggered packet-level reporting allows security teams to conduct a highly targeted forensic analysis.
The entire breach investigation can typically be completed within an hour – assuring compliance.
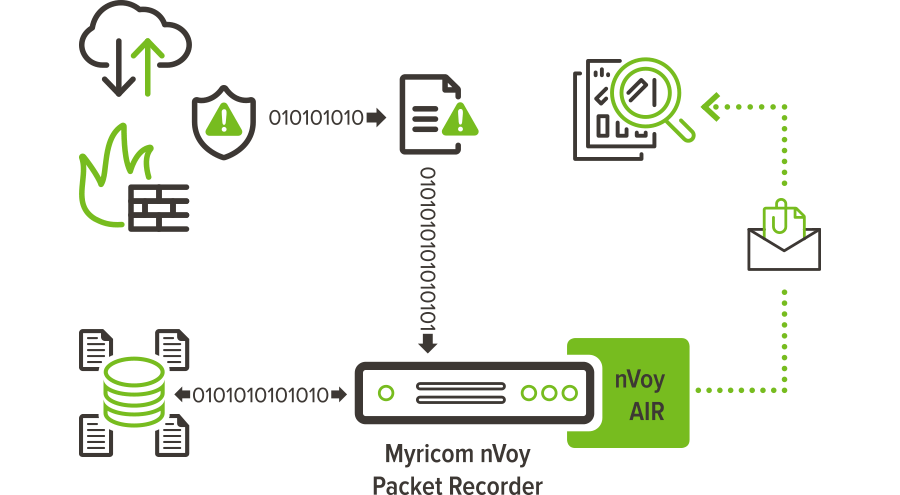
Answer the most critical questions related to meeting regulatory compliance:
- What devices are involved?
- When did the breach start? When did it end?
- What exact files and databases were accessed
- Who did the intruder talk to?
Finally, an Automated Breach Response Solution that Works
Resources and Related Content
Resources
Blog
News
ARIA Cybersecurity Solutions, a leading provider of cybersecurity solutions, recognizes Information Systems for Trading (IST) as a premier reseller in the Jordan and Iraqi…
ARIA Cybersecurity Solutions has joined Rockwell Automation’s PartnerNetwork™ as a Technology Partner. Through PartnerNetworkTM, customers can quickly locate complementary products that best solve application…
ARIA Cybersecurity Solutions, a CSPi business (NASDAQ: CSPi), has announced that its breakthrough solution for protecting Operational Technology (OT) environments, AZT PROTECT™, has won…
Events