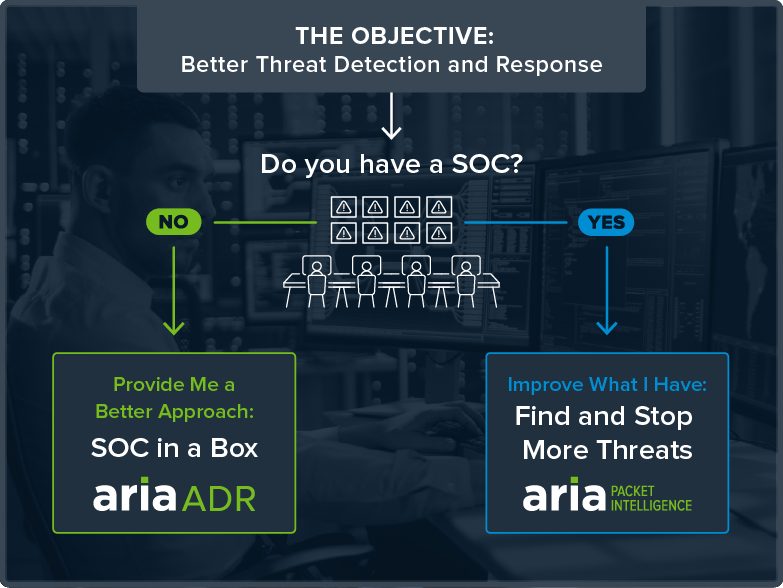
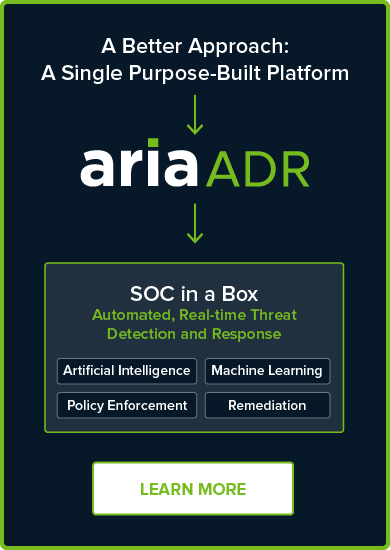
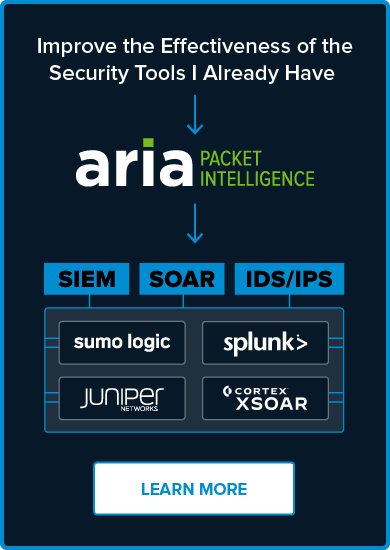
Cybersecurity Products
Better Cybersecurity Starts With A Smarter Approach
Contact Us to Speak to a Cybersecurity Expert!
Resources and Related Content
Resources
Blog
February 29, 2024
UnitedHealth Group’s Optum Subsidiary disrupted by Cyberattack | ARIA Cybersecurity
A major cyberattack has just hit the systems of a subsidiary of US health insurance giant, UnitedHealth. In an SEC filing, UnitedHealth said that…
February 5, 2024
How to Protect Against Supply-Chain Attacks | ARIA Cybersecurity
SUNBURST (SolarWinds) – How ARIA would have stopped the supply-chain cyberattack of the decade – and others like it
January 31, 2024
Protecting OT From Unknown Vulnerably Exploits | ARIA Cybersecurity
The new generation of cybersecurity defenses must protect against never-seen-before attacks even before they are devised by the attackers. In early December 2023,…
News
April 18, 2024
ARIA Cybersecurity Expands Global Reach of Cybersecurity Product Portfolio
ARIA Cybersecurity Solutions, a leading provider of cybersecurity solutions, recognizes Information Systems for Trading (IST) as a premier reseller in the Jordan and Iraqi…
March 21, 2024
ARIA Cybersecurity Brings Breakthrough Critical Infrastructure Cybersecurity Solution to Rockwell Automation Partner Ecosystem
ARIA Cybersecurity Solutions has joined Rockwell Automation’s PartnerNetwork™ as a Technology Partner. Through PartnerNetworkTM, customers can quickly locate complementary products that best solve application…
March 12, 2024
ARIA Cybersecurity Wins Globee Cybersecurity Product Award for AZT PROTECT
ARIA Cybersecurity Solutions, a CSPi business (NASDAQ: CSPi), has announced that its breakthrough solution for protecting Operational Technology (OT) environments, AZT PROTECT™, has won…
Events
May 9, 2024
Hear from Rockwell about the unique set of requirements that are needed to protect your production application’s attack surface and how Aria’s AZT Protect…
March 26, 2024
At CS4CA, ARIA GM Gary Southwell will share how companies in critical infrastructure sectors can minimize financial, regulatory, and reputational risk in today’s new…
January 24, 2024
Join Gary Southwell, chief executive of ARIA Cybersecurity and retired Pfizer global head of automation engineering Jim LaBonty for a wide-ranging discussion of the…
ARIA Cybersecurity Inks Major Reseller Agreement to Drive Adoption of Breakthrough OT Cybersecurity Solution
Read More!